Nworm: TrickBot gang’s new stealthy malware spreading module
by Lawrence Abrams
The Trickbot banking trojan has evolved once again with a new malware spreading module that uses a stealth mode to quietly infect Windows domain controllers without being detected.
Started as a banking Trojan, the TrickBot malware has evolved with the constant addition of new modules that allows it to perform a variety of malicious behavior.
Some of this behavior includes spreading laterally through a network, stealing Active Directory Services databases, stealing cookies and OpenSSH keys, stealing RDP, VNC, and PuTTY Credentials, and more.
TrickBot also partners with ransomware operators, such as Ryuk, to gain access to a compromised network so they can deploy ransomware.
Meet Nworm: TrickBot malware's stealthy propagation module
In a new report by Palo Alto Unit 42, researchers discovered that the TrickBot developers had released an updated network spreading module called 'nworm' that uses new techniques to evade detection as it infects Windows domain controllers.
When installed, TrickBot will assess the environment that it is running in and then download various modules to perform specific malicious activity on the infected computer and in the network.
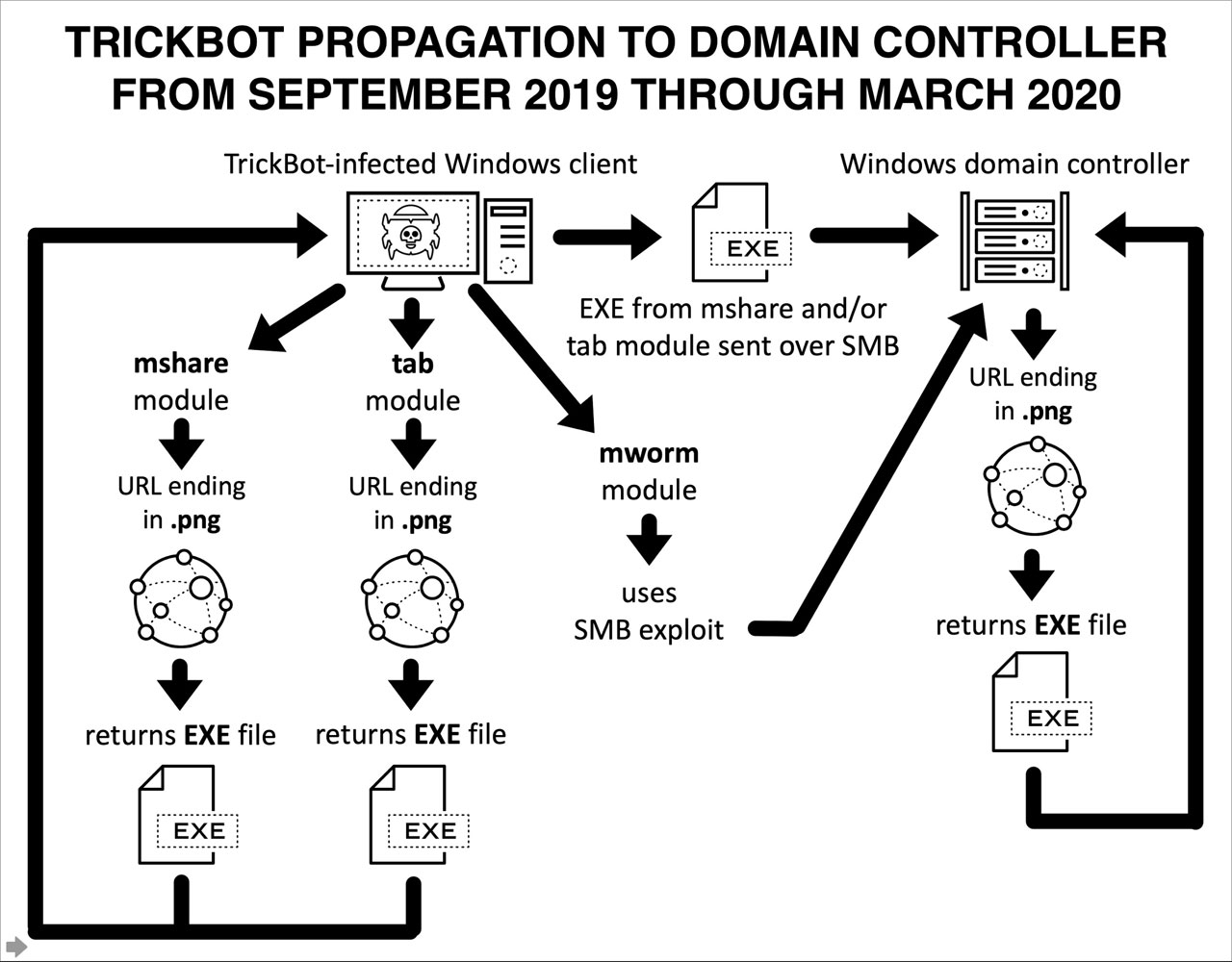
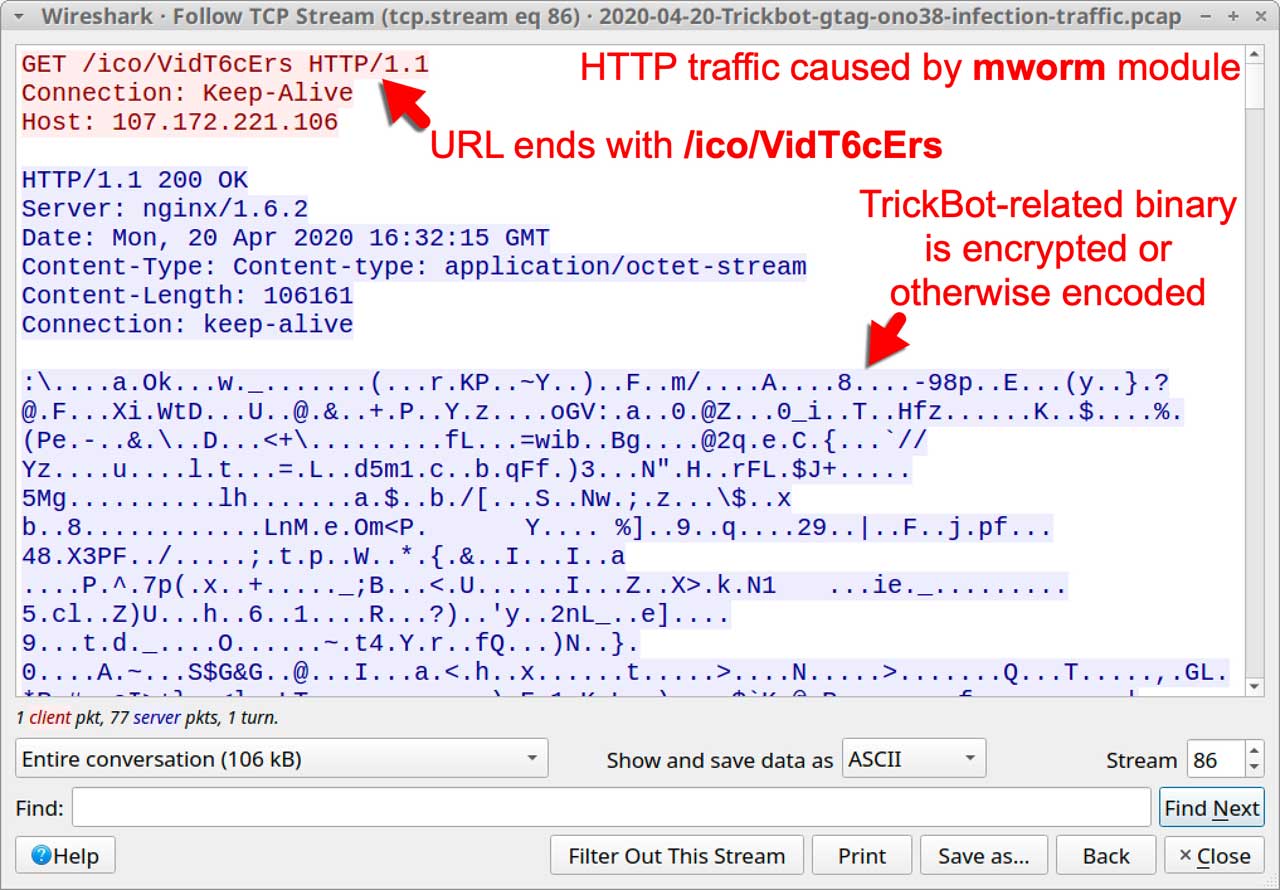
If TrickBot detects that it is running in a Windows Active Directory (AD) environment, it has historically downloaded modules called 'mworm' and 'mshare' used to spread the TrickBot infection to a vulnerable domain controller.
The module does this by attempting to exploit SMB vulnerabilities in the domain controller.
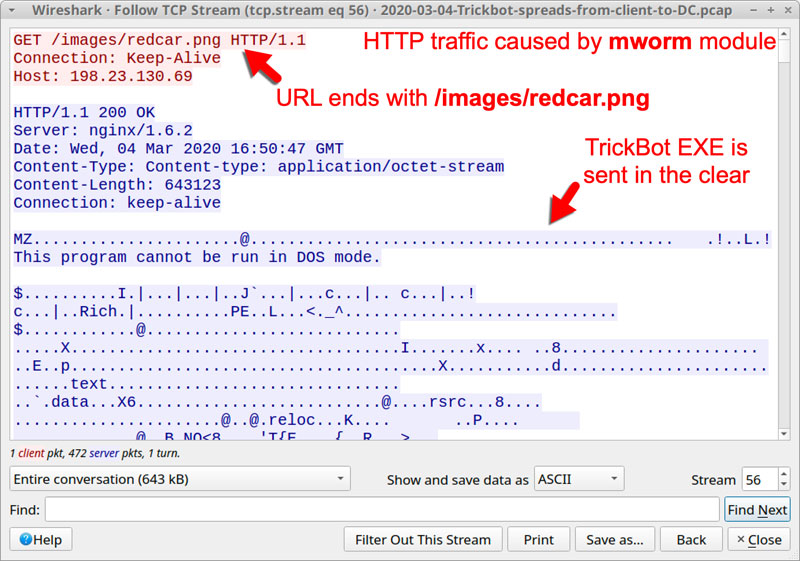
From September 2019, when TrickBot began using Mworm, through March 2020, the mworm module would transfer the TrickBot executable in an unencrypted form to a vulnerable domain controller.
Source: Palo Alto Unit 42
As the malware executable would be unencrypted, security software installed on the DC could detect it and remove it right after being copied.
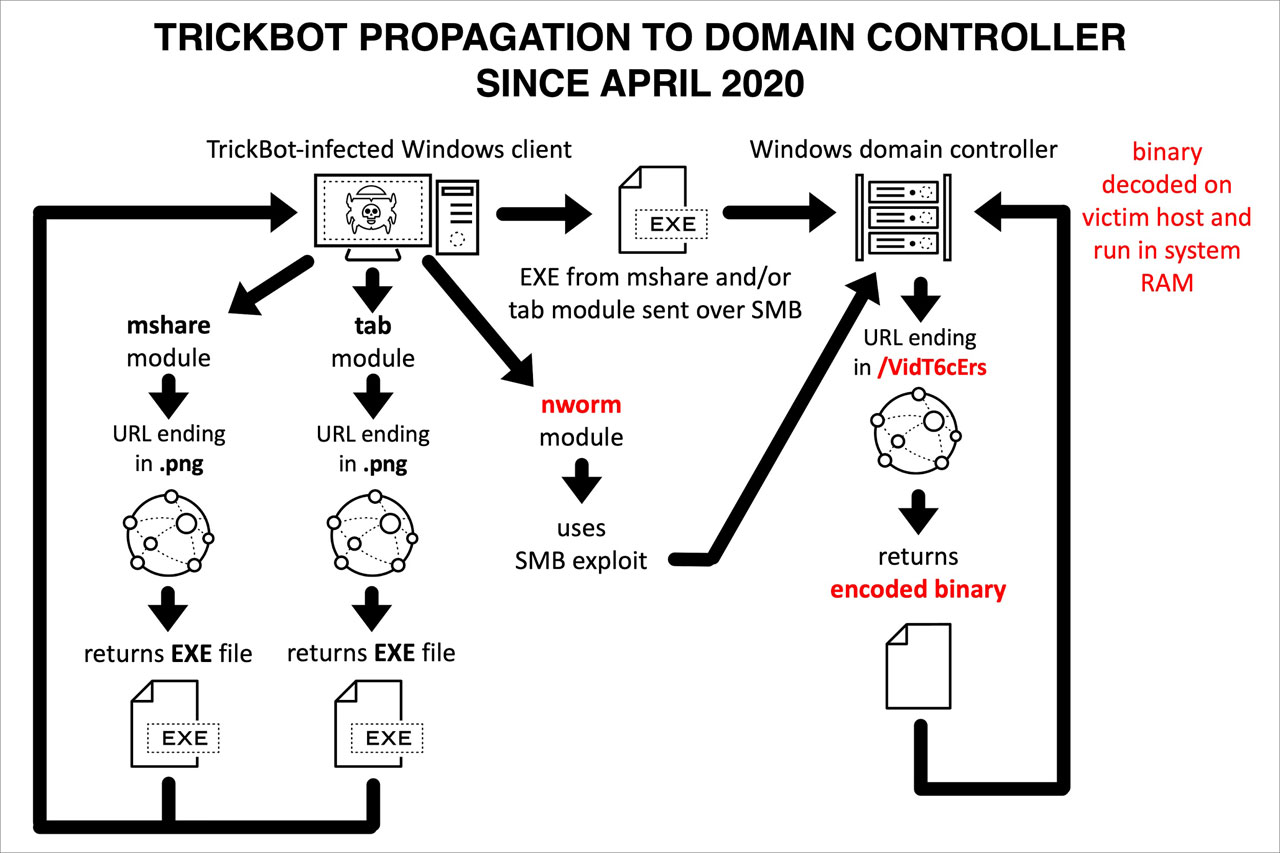
To make it harder to be detected, in April 2020 the TrickBot developers released an updated worm module called 'Nworm',
"In April 2020 while generating a TrickBot infection in a lab environment, TrickBot stopped using the mworm module. In its place, a new artifact named “nworm” appeared on an infected Windows 7 client," the researchers explain in their report.
Source: Palo Alto Unit 42
This new nworm module not only encrypts the TrickBot executable so it can't be detected by security software, but also launches the infection on the domain controller in memory.
Using this method, TrickBot can be snuck into a domain controller and executed without being detected.
Source: Palo Alto Unit 42
To further increase its stealthiness, when infecting a domain controller, the TrickBot malware will not remain persistent to start again if the computer is rebooted.
As domain controllers are rarely restarted, this should not pose a problem as the infection should stay running in memory for an extended period.
This is usually enough time for the threat actors to execute and complete their attack.