Valak malware steals credentials from Microsoft Exchange servers
by Ionut Ilascu
Classified initially as a malware loader, Valak has morphed into an information stealer that targets Microsoft Exchange servers to rob email login credentials and certificates from enterprises.
Its original functionality remains, so it can still deliver other malware (banking trojans Ursnif and IcedID), but it now has plugins to run reconnaissance and steal sensitive info from the target.
Rich modular architecture
Valak evolved quickly since it was first noticed in late 2019, with more than 30 versions being detected in less than six months.
New variants of this malware family used in recent campaigns indicate significant improvements and a preference for enterprise environments, mainly companies in the U.S. and Germany.
Researchers at cybersecurity company Cybereason determined that the capabilities in the latest Valak samples include checking the geographical location of an infected machine, taking screenshots, downloading other payloads (plugins, malware), infiltrating Microsoft Exchange servers.
Valak hides its payloads, command and control (C2) details and other components in the registry. In later stages of the attack, it taps into the cache to pick the tools it needs for various tasks.
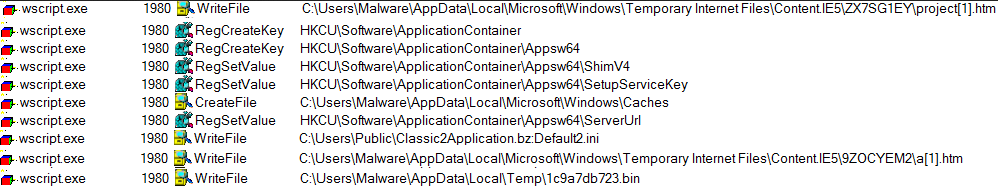
Campaigns delivering Valak start with an email delivering a Microsoft Word documents that have malicious macro code inside. The documents are created in the language of the target.
The malware achieves persistence by scheduling a task to run Windows Script Host (wscript.exe) and execute JavaScript stored as an Alternate Data Stream.
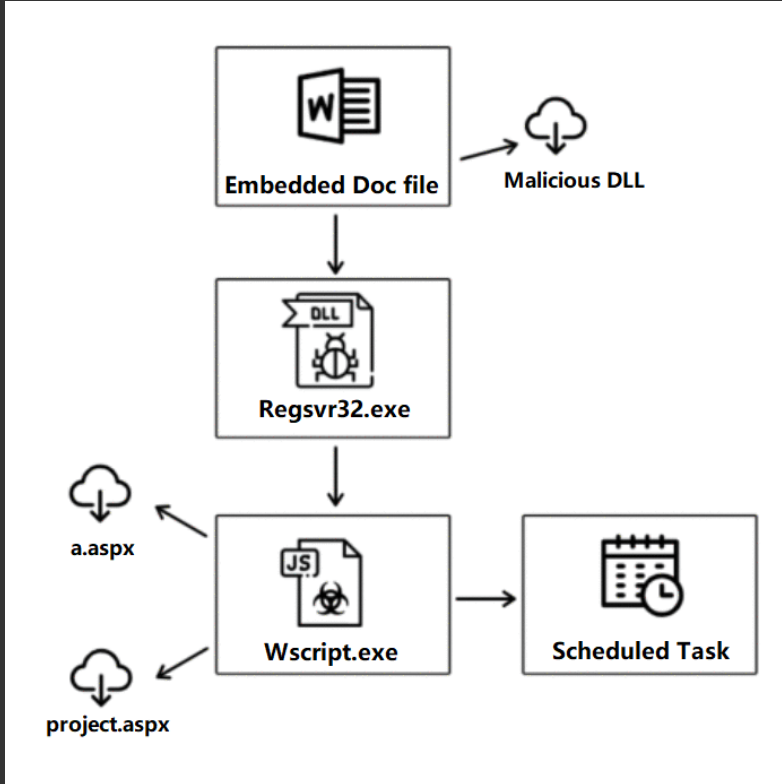
More modules are downloaded in the second stage, to explore the environment and steal sensitive information. All of them are available under the same internal name, “ManagedPlugin.dll.”
They are fetched and loaded by “PluginHost.exe” and their names hint at their functionality: Exchgrabber, Systeminfo, IPGeo, Procinfo, Netrecon, Screencap.
Domain passwords and certificates
“Exchgrabber“ is responsible for taking Microsoft Exchange data and to infiltrate the company email system. Looking at its classes, the module seems to handle only credential stealing.
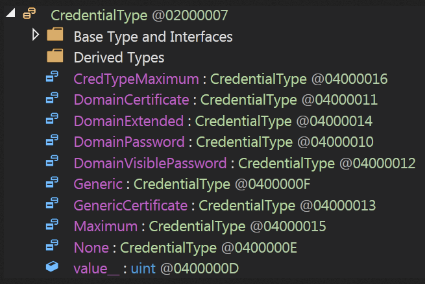
However, the researchers found that there is more to it. A function called “CredentialType“ has all the credentials that the module will try to extract.
The sensitive data includes not only usernames and passwords but also domain passwords and certificates. The risk is obvious, as the researchers explain in their analysis.
“Extracting this sensitive data allows the attacker access to an inside domain user for the internal mail services of an enterprise along with access to the domain certificate of an enterprise” - Cybereason
With the "systeminfo“ module, attackers using Valak malware can determine the domain administrators, which can lead to ”large-scale spying or infostealing.“
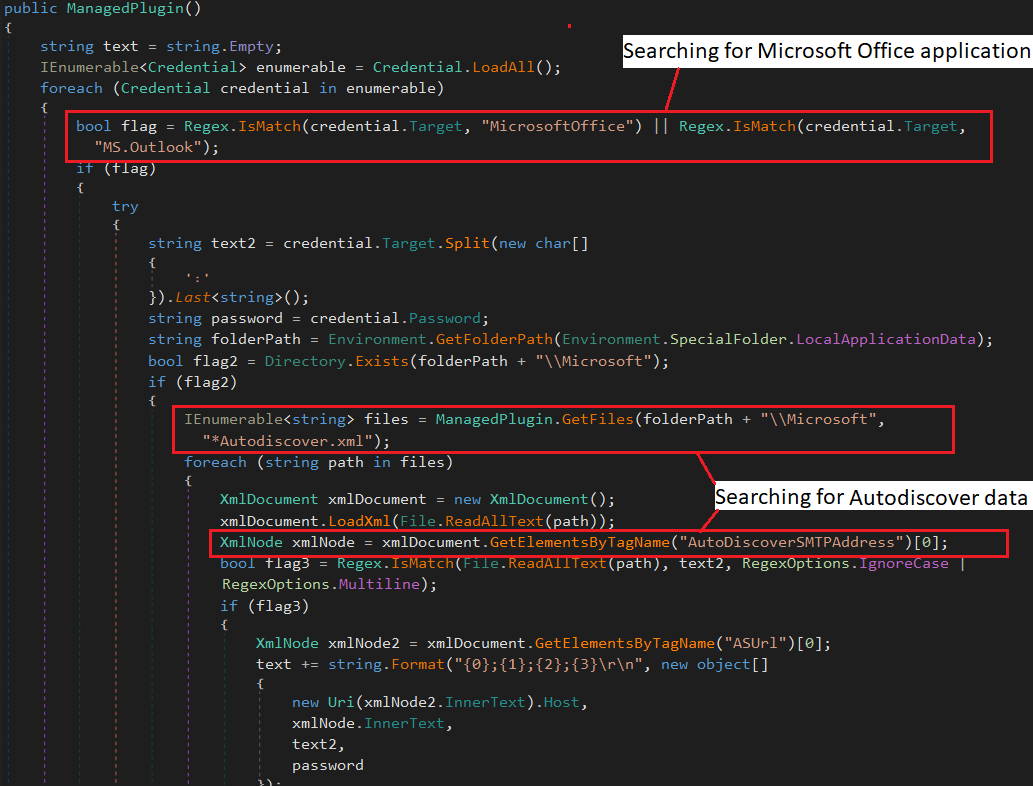
The researchers also found that Valak’s plugin also allows discovering if the data is for Microsoft Office or for logging into Outlook.
This is done by accessing the “Autodiscover.Xml” file with data needed by Outlook to access user mailboxes on Exchange.
Malware developers have created a sophisticated tool that can function on its own. Valak’s six-month rapid development cycle turned into a modular threat that can scout the target environment, collect sensitive data, and serve other malware.
Cybereason found more than 50 command and control servers used with different Valak versions. It appears that they have a shared infrastructure as all known domain names are linked to one another via downloaded files, URI similarities, or connected files.
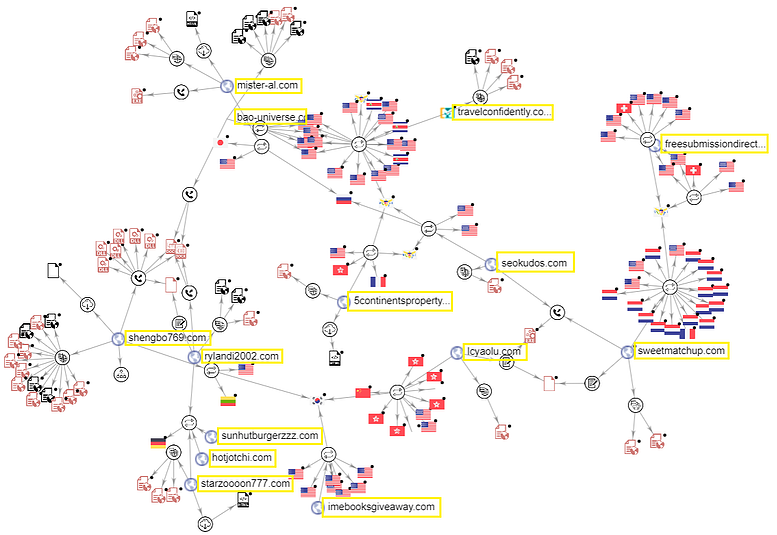
Based on the observed partnership with Ursnif and IcedID, Valak may also have a Russian cybercrime origin. Its authors are likely members of the same underground community. However, a clear connection has not been established at the moment.
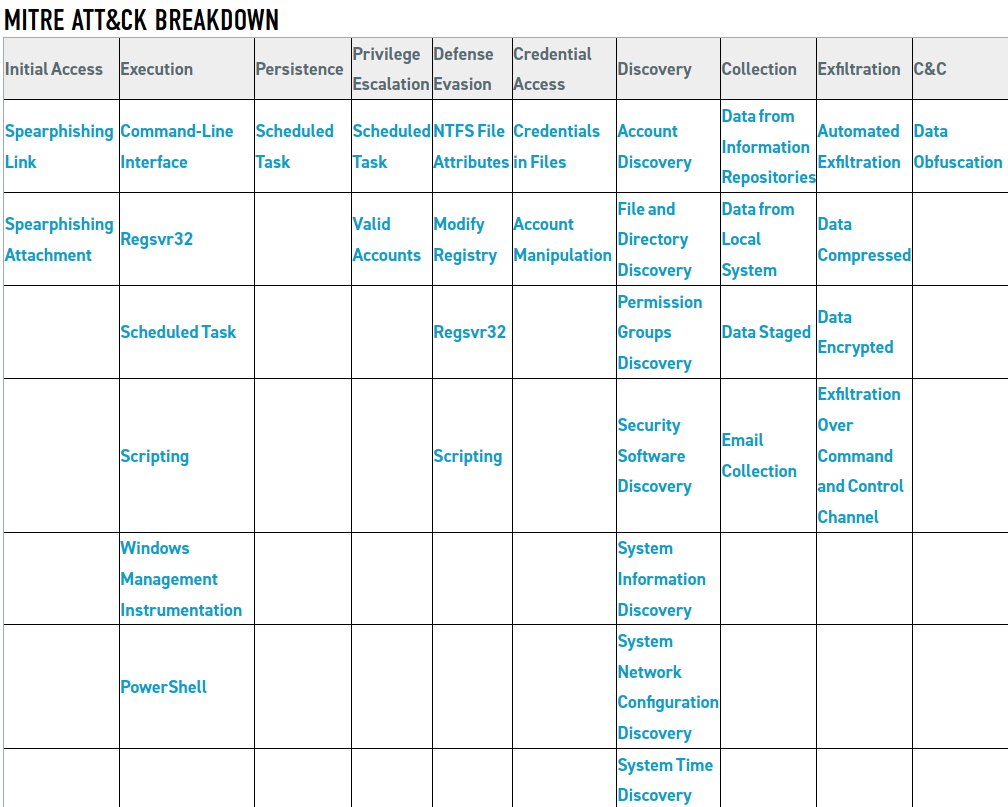
Cybereason created the Valak attack matrix that is rooted on their observations. A complete analysis of the maware and its modules is available here. Indicators of compromised are available in this PDF file.