Highly-targeted attacks on industrial sector hide payload in images
by Ionut Ilascu
Attackers looking to steal employee credentials from organizations tied to the industrial sector deployed highly-targeted operations that delivered malicious PowerShell scripts in images.
The technique is called steganography and in these incidents the actors used public hosting imaging services to evade network traffic scanners and control tools that would flag the malicious download.
Payload tailored to target's language
Victims in multiple countries (Japan, the U.K., Germany, Italy) were identified. Some of them supply equipment and software solutions to industrial enterprises.
The attacks started with a phishing email containing a Microsoft Office document with malicious macro code whose role is to decrypt and execute an initial PowerShell script.
They adapted to the geographic diversity of the targets by creating messages and documents in the language specific to each victim and the malware carried its tasks only on systems that matched the locale of the email.
Several parameters enable the script to run in a hidden window (-WindowStyle Hidden) regardless of the configured policy (-ExecutionPolicy Bypass) and without loading the user configuration (-NoProfile).
The purpose of this first PowerShell script is to download an image from randomly selected addresses on Imgur or Imgbox hosting services and begin extracting the payload.

The payload hidden in the image is encoded with Base64, encrypted with RSA, and encoded once more using Base64. A deliberate error in the script generates an exception message that is the decryption key.
Security researchers at Kaspersky ICS CERT analyzing these attacks saw that the exception message also depends on the language on the target operating system.
The data concealed in the images decrypts to a second PowerShell script that further decodes some of its contents, which reveal a sample of Mimikatz open-source application for getting access credentials on Windows.
Below is the full attack chain observed by Kaspersky:
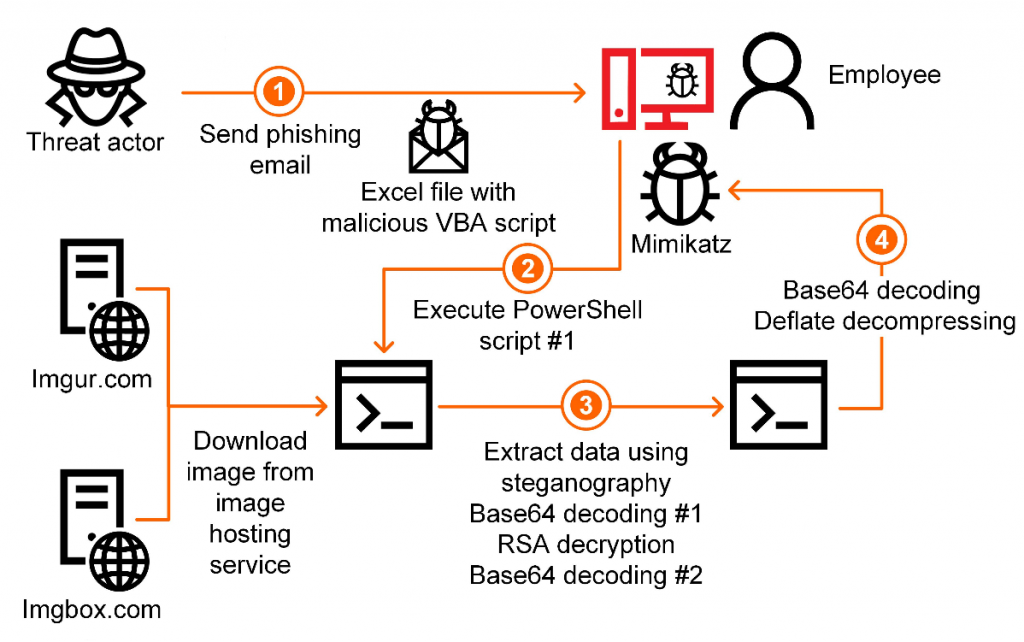
Using steganography and public image hosting services allows the threat actor to pass their payload undetected by network security solutions. The custom exception message bypasses automatic analysis of the malware and also makes it more difficult for researchers to check it.
“It is a matter of concern that attack victims include contractors of industrial enterprises. If the attackers are able to harvest the credentials of a contractor organization’s employees, this can lead to a range of negative consequences, from the theft of sensitive data to attacks on industrial enterprises via remote administration tools used by the contractor” - Kaspersky
Avoiding these attacks starts from blocking initial access. Phishing is the most common method to get malware onto a target’s network. Defending against attack vector by training employees to spot suspicious messages is a good step towards an improved security stance.
Macro code is disabled by default in Microsoft Office documents specifically to prevent malware infections and PowerShell is regularly used by threat actors to run commands for fetching and executing payloads; restricting it when possible only strengthens the defenses.
Kaspersky also recommends the following action for increased protection:
- Watch events that launch PowerShell processes initiated by Microsoft Office apps
- Restrict the ability of programs to gain SeDebugPrivilege privileges (wherever possible)
- Get an antivirus with central management of security policies on all systems and keep it updated
- Domain administrator accounts should be used only when necessary and systems should be restarted after authentication
- Implement a password policy with password strength and regular password change requirements
- If there’s a suspicion that some systems are compromised, an antivirus scan is in order and passwords should be changed for all accounts that logged on the computer