Ransomware's big jump: ransoms grew 14 times in one year
by Ionut Ilascu
Ransomware has become one of the most insidious threats in the past couple of years, with actors scaling up their operations to the point that the average ransom demand increased more than 10 times in one year.
There are well over a dozen operators in the ransomware-as-a-service (RaaS) game, each with a host of affiliates that focus on enterprise targets across the world.
Since the infamous GandCrab group called it quits in mid-2019, the ransomware landscape changed drastically. The RaaS model they introduced is now the norm, paving the way for professional attackers with a clear strategy to make money.
Huge jumps in ransom demand
The year-over-year evolution of the ransomware threat is visible in terms of the ransom demand as well as the tactics, techniques, and procedures (TTPs) used by the attackers running big-game ransomware operations.
In a report today, cybersecurity company Group-IB analyzed how this threat changed in just one year since 2018. They adopted a wide range of initial access vectors, increased their ransom demands, and started to steal files from victims before encryption for further leverage to force a payment.
According to the report, ransomware attacks in 2019 increased by 40% and the focus on larger targets drove the ransom price from $6,000 to $84,000, two of the greediest families being Ryuk and REvil (Sodin, Sodinokibi).
In 2020, though, the price has increased even more. Data from Coveware, a company that handles ransomware incidents, shows that the average increased in the first quarter of the year even more, to $111,605. Ryuk and REvil continue to be responsible for this increase in average ransom.
Tactics, techniques, and procedures
Among the most common intrusion techniques that the Singapore-based company observed in incident response engagements, drive-by compromise via exploit kits (EKs), external remote services (mainly RDP), and spear phishing were at the top of the list.
At the RSA security conference in February, the FBI also stated that RDP is the most common method ransomware actors use for access to the victim network.
"RDP is still 70-80% of the initial foothold that ransomware actors use," said FBI Special Agent Joel DeCapua.
More advanced ransomware actors relied on methods that gave them access to more valuable targets: supply-chain compromise, exploiting unpatched vulnerabilities in public-facing applications, or compromising managed service providers (MSPs).
From there, the attackers deployed their tools and moved to the next stages establishing persistence, escalating privileges (if needed), evading defenses, acquiring credentials, mapping the network, moving to valuable hosts, stealing files, and then encrypting them.
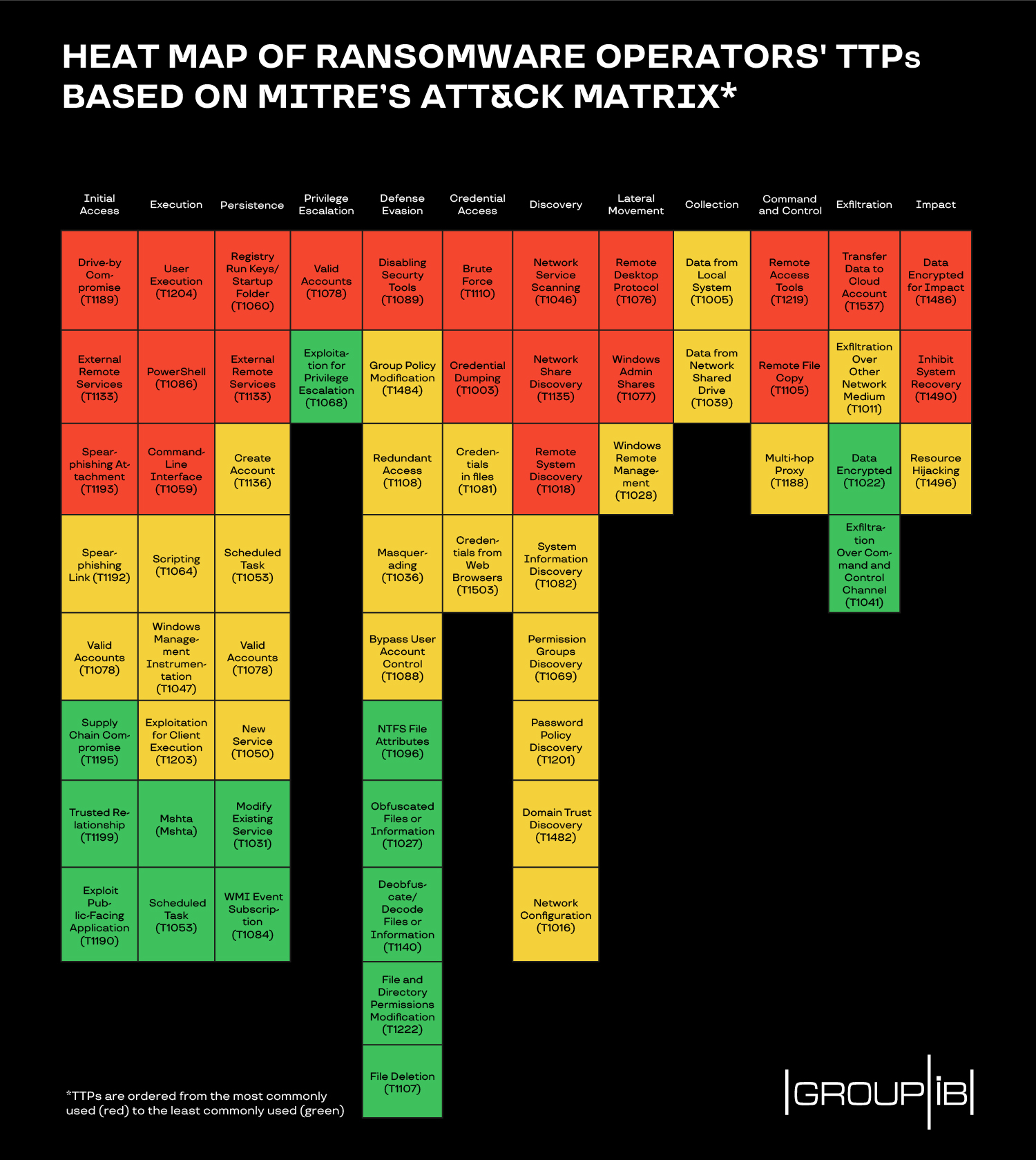
Group-IB's whitepaper details that even big-league players like Ryuk, LockerGoga, REvil, MegaCortex, Maze, or Netwalker used common intrusion methods such as RDP simply because the access to servers with an open port was easy to get from marketplaces.
Phishing is also used regularly to gain initial access to a company's network. Normally, networks that distribute malicious emails like Emotet, Trickbot (Ryuk), or QakBot (ProLock, MegaCortex) are used to for access to the target network.
Advanced actors extended their tactics to exploiting bugs in WebLogic Server (CVE-2019-2725) or Pulse Secure VPN (CVE-2019-11510); this was seen in REvil attacks.
Recently, though, at least one ransomware actor is taking their operation to another level. NetWalker ransomware group started looking for affiliates with network access to huge businesses.
Steal > encrypt > leak
While the intrusion techniques have not changed much since 2019, the list of ransomware operators has grown steeply and some of them switched to new names:
- JSWorm became Nemty in August 2019
- Mailto became Netwalker in February 2020
- Cryakl is now CryLock
- PwndLcker rebranded to ProLock in March 2020
Even more of them started to leak files stolen from victims unless they got their ransom. This trend was started by Maze in November 2019, when they published data from Allied Universal.
At the moment, 12 ransomware operators have leak sites where they publish data stolen from victims, while others use hacker forums to share download links.
Some of the ransoms demanded by the attackers have mind-blowing proportions. REvil, for instance, asked for $21 million from a victim or they would publish data about the company's clients, most of them being big names in the entertainment industry.
Ako ransomware, another actor that also steals victim data, found a way to increase their profits by asking for two ransoms: one for decrypting the files and another for not publishing the stolen files.
Ransom demands of $1 million and more are no longer uncommon as threat actors adjust their prices according to the compromised organization’s revenue and the number of locked computers.
Last year was highly profitable for ransomware actors but with the prices we've seen recently, 2020 is likely to surpass it as actors continue to target large companies in key industries.