26 million LiveJournal accounts being shared on hacker forums
by Lawrence Abrams
A database containing over 26 million unique LiveJournal user accounts, including plain text passwords, is being shared for free on multiple hacker forums.
For some time, rumors have been circulating that LiveJournal was breached in 2014 and account credentials for 33 million users were stolen.
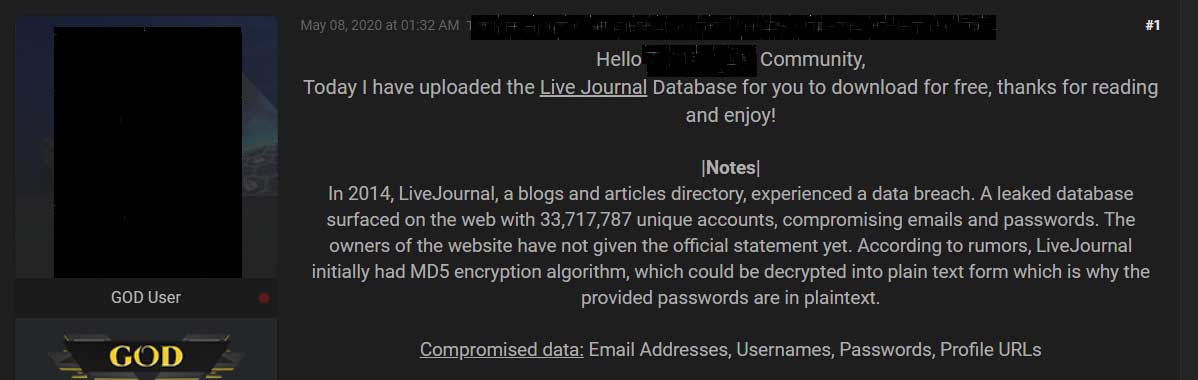
Since approximately May 8th, 2020, links to a data dump allegedly containing 33,717,787 unique accounts have been circulating on various hacker forums.
According to posts sharing the links, the database dump contains email addresses, usernames, profile URLs, and passwords. The passwords were converted to plain text after initially being stored as MD5 hashes.
Today, numerous people have shared the alleged LiveJournal database with Troy Hunt of Have I Been Pwned, who added it to their data breach notification service.
Hunt has told BleepingComputer that it appears to be the same data breach that was discussed last year.
Instead of classifying the data breach as being from 2014, though, Hunt is stating it is from 2017 based on the data dump's file name of 'LiveJournal_com_2017_33.7M.txt.'
"There's contradictory info: the Forum post says 2014 but then the file I sent you a screen cap of says 2017. There's no time stamps in the file to make it any clearer but the earliest evidence I have (based on community feedback) is 2018."
"I generally err on the side of the later date otherwise you end up with people saying "I didn't create an account until 2016 and I'm in there so you have the date wrong"," Hunt told BleepingComputer.
BleepingComputer was able to find links to the circulating database within five minutes of talking to Hunt.
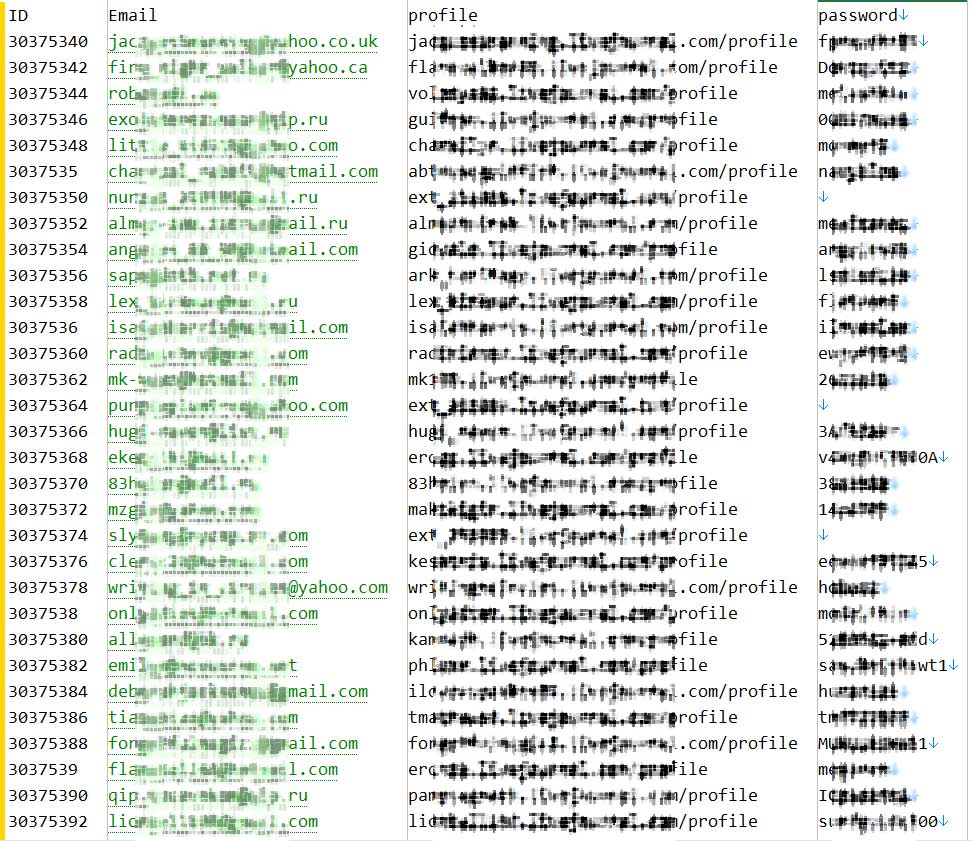
BleepingComputer has since been able to independently confirm with a few people that information for old accounts was accurately included in the database.
LiveJournal has denied being compromised
Denise Paolucci replied to Hunt's tweet today, stating that her company Dreamwidth Studios has been dealing with credential stuffing attacks that overlap with the credentials in the LiveJournal database.
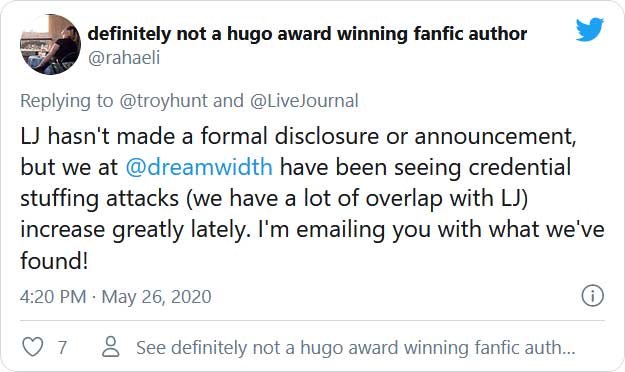
Paolucci shared links to Dreamwidth maintenance bulletins with BleepingComputer from 2017 and 2018 that indicate that credentials from this LiveJournal database were used in credential stuffing attacks.
In the 2017 maintenance bulletin, two customers referenced that their accounts at LiveJournal had been compromised.
"LiveJournal refugees should be especially careful not to reuse their passwords from there. A large number of people I know, including myself, got "Caught you on camera watching porn" spam, giving our old LiveJournal passwords as "evidence." In its earlier days, LJ must have been very sloppy about protecting user passwords," a customer posted.
"Let me be scrupulously careful here in how I phrase this: There are files ("dumps") on the black market that claim to be from a LiveJournal breach in 2014, and I've never seen anyone who was listed in the dumps say that their information was incorrect (and have seen many who have said it was)," Paolucci responded.
To this day, LiveJournal has never confirmed that a data breach has occurred or that the database is legitimate.
BleepingComputer has emailed LiveJournal about the circulating database but has not heard back at this time.
What should LiveJournal users do?
Hunt has added the database to the Have I Been Pwned data breach notification service, and users can use it to confirm if their email address is part of the database.
If the service shows that your email address was included, you should immediately change your passwords on LiveJournal to be safe.
This database is potentially six years old, so it hoped that users would have changed their password over the years, but to be safe, do so again.
If you use the same password at other sites, be sure to switch to a unique and complex password at these other sites.