Hacker extorts online shops, sells databases if ransom not paid
by Ionut Ilascu
More than two dozen SQL databases stolen from online shops in various countries are being offered for sale on a public website. In total, the seller provides over 1.5 million rows of records but the amount of stolen data is much larger.
The attacker is hacking into insecure servers that are reachable over the public web, copies the databases, and leaves a note asking for a ransom in return of the stolen data.
Money made
Victims have 10 days to pay BTC 0.06 ($525 at current price) a wallet provided in the ransom note, else the hacker makes the database public or uses it as they please.
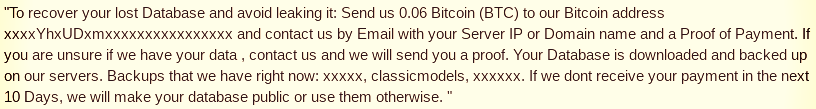
A couple of wallets used by the attacker recorded more than 100 received transactions for a combined total of BTC 5.8 (currently worth a little over $51,000).
The number of abuse reports for these two wallets is over 200, the oldest being from September 20, 2019. The most recent one is from May 20 and this month alone there were nine reports, indicating that the actor is highly active.
It is important to note that the hacker may use more than the wallets found by BleepingComputer. Also, the number of abuse reports for the bitcoin addresses used by hacker are not indicative of the full activity of the operation. Not all victims report the attacker and some decide to pay the ransom.
E-commerce platforms targeted
There are 31 databases listed on the website, although judging from the number of abuse reports, this is clearly just a small portion. The most recent one is from March, and all have a sample attached for the potential buyers to check.
Two more databases are unlisted, one of them advertised in April on a hacker forum, and another stored in the "/samples" directory of the website.
More than half of the listed databases are from online stores in Germany; others are from Brazil, the U.S., Italy, India, Spain, and Belarus. All run e-commerce platforms like Shopware, JTL-Shop, PrestaShop, OpenCart, Magento v1 and v2).
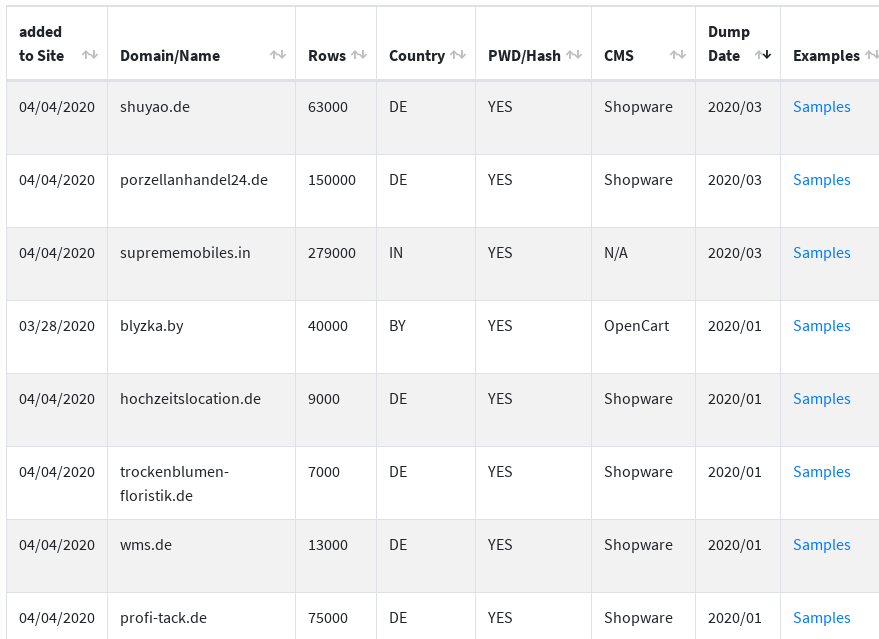
The total number of rows available in these databases is around 1,620,000. Depending on the store, the data contains email addresses, names, hashed passwords (e.g. bcrypt, MD5), postal addresses, gender, dates of birth.
Some of the databases have a dump date from 2016 but the site seems to have been populated starting March 28, 2020.
This type of attack is reminiscent of the MongoDB ransom attacks that peaked in 2017 and continued through 2019 (1, 2, 3, 4); and here's an old one targeting MySQL servers.
Guardicore researcher Ophir Harpaz spotted at the beginning of the year a ransomware campaign targeting MySQL servers. The intruders brute-forced they way into the server and encrypted the databases; then they created a 'Warning' table to drop their ransom note. About 50 attacks were detected.
Databases are still attractive to cybercriminals. Despite having a low financial value compared to other types of extortion, the crooks can increase their profits by selling the data to multiple parties, including the victim.
h/t Ninja Null