Mobile Phishing Campaign Uses over 200 Pages to Spoof Bank Sites
by Ionut Ilascu
A phishing campaign focused on mobile banking used over 200 pages to impersonate legitimate websites for well-known banks in the U.S. and Canada.
Thousands of victims were lured to the fake sites with short messages delivered through an automated tool in the phishing kit.
Major banks targeted
In an effort to capture banking credentials, the cybercriminals spoofed login pages for at least a dozen banks, say in a report today security researchers at mobile security company Lookout.
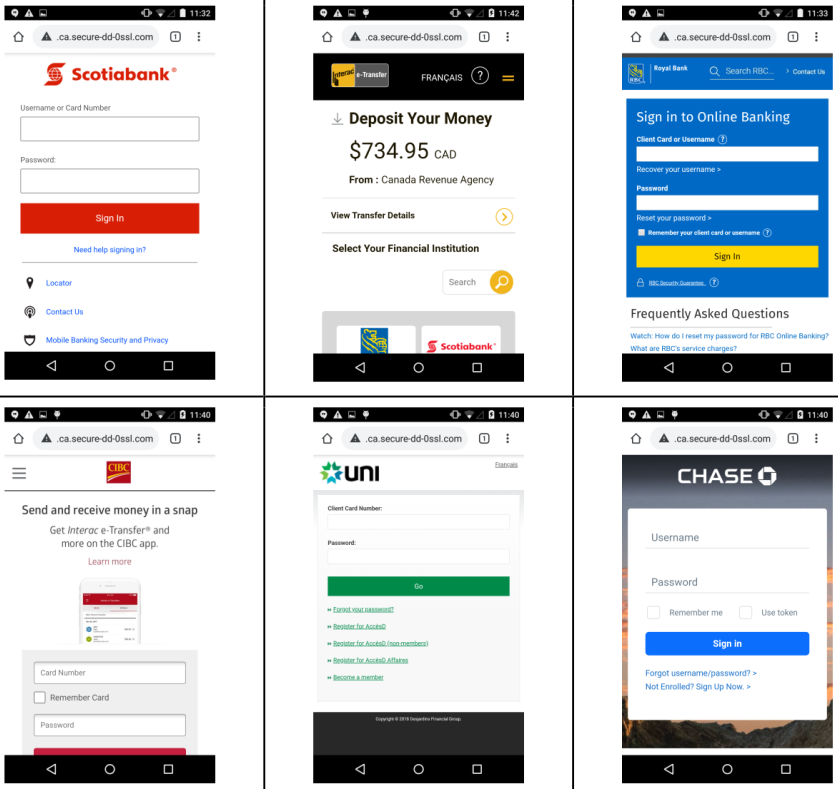
The list of targeted banks includes major players on the market like Scotiabank, CIBC, RBC, UNI, HSBC, Tangerine, TD, Meridian, Laurentian, Manulife, BNC, and Chase.
According to the research, the phishing pages were created specifically for mobile, mimicking the layout and sizing. In their attempt to trick victims, the crooks also used links such as "Mobile Banking Security and Privacy" and "Activate Mobile Banking."
Apart from increasing confidence in the page, these links might also be used to collect sensitive information by asking for the credentials when accessing them.
The cybercriminals behind this campaign used an automated SMS tool available in the phishing kit to deliver custom messages to numerous mobile phone numbers.
This suggests a mobile-first attack strategy, Lookout researchers say. It may also contribute to the success of the campaign since users expect bank communication via SMS.
"Many of the pages in this campaign appear legitimate through actions like taking the victim through a series of security questions, asking them to confirm their identity with a card’s expiration date or double-checking the account number" - Lookout
Spoofed pages accessed from thousands of IPs
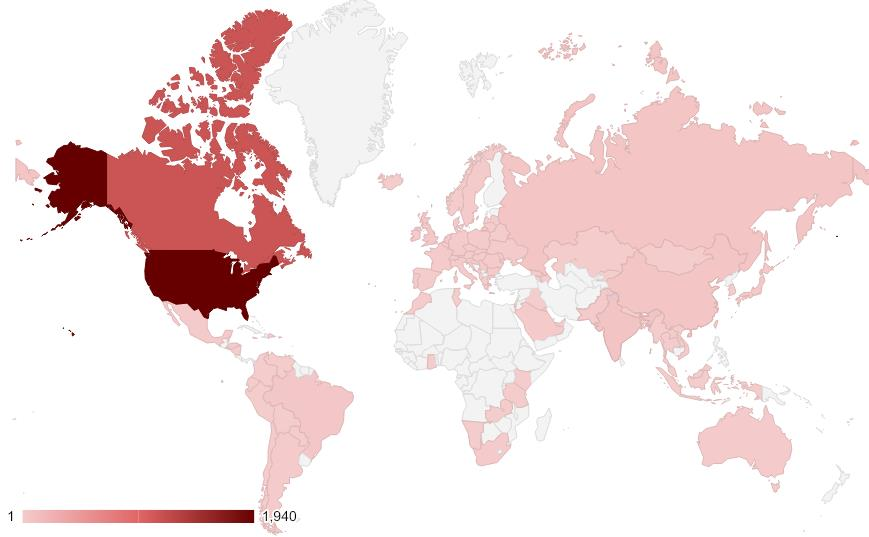
Victims of this campaign spread all over the world, as researchers found on phishing pages lists of IP addresses belonging to devices that accessed the malicious link.
Additional details available included how far the victims went and if they were completely duped by the scam. From these statistical data, crooks could see what information was collected, such as account number and date of birth.
The security company identified more than 200 phishing pages that were created for this campaign. Since June 27, 2019, the malicious links were accessed from over 3,900 unique IP addresses, most of them in North America.
The campaign is no longer active and Lookout contacted all targeted banks about the impersonation attempts.
Avoiding these scams is more difficult on mobile than on a desktop computer because the limited space on the screen plays to the attacker's advantage.
However, there is a simple trick that can save you from becoming a victim of a mobile phishing attempt: instead of clicking on a link you get in a text message, type it yourself in a browser or launch the bank's app if you have it on the device.