Outbreak Of Android Trojan xHelper Malware Appears To Be Triggered By Google Play Itself
by Brittany Goetting
Android Trojan xHelper haunted the Google Play Store in 2019. After several months, it appeared that the malware had disappeared. Unfortunately, xHelper was not dead but only sleeping. Security researchers at Malwarebytes Lab recently discovered that xHelper was once again infecting devices and that its reinfection seemed to be triggering off from Google Play.
Android Trojan xHelper first appeared in Spring 2019 and infected over 45,000 devices. xHelper targeted users in India, the United States, and Russia. It is a malware dropper whose main purpose is to provide a backdoor to attackers. The attackers can then install other apps, steal data, or even take over the device.
A Malwarebyte forum user named “misspaperwait” aka Amelia, recently noticed that xHelper was still infecting her device. The Malwarebytes for Android mobile app had already removed several forms of the virus and Amelia had even performed a factory reset. Unfortunately, xHelper maintained a firm grip on her device.
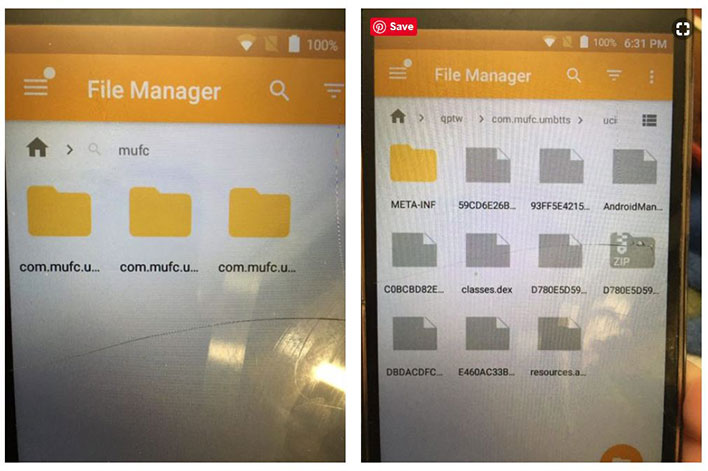
Malwarebyte researchers first suspected that pre-installed malware was to blame for the reinfection. They eventually discovered several folders named “com.mufc…” These folders had not been removed with the factory reset. Researcher Nathan Collier further noted, “Hidden within a directory named com.mufc.umbtts was yet another Android application package (APK)...It is responsible for dropping one variant of xHelper, which subsequently drops more malware within seconds.”
The researchers also discovered that the malware claimed it was coming from Google Play. Although Google Play itself was not infected, the xHelper reinfection appeared to be triggered to reinstall itself by Google Play. The researchers are unsure of the malware’s source and argued that it could be using Google Play as a “smokescreen”. Regardless of the source, the reinfection halted once Amelia had disabled Google Play.
They currently recommend that users download their mobile app to scan for malware and install a reliable file manager that is able to search files and directories. They then suggest disabling Google Play and using the file manager to search for anything with the label “com.mufc”. Users should delete these files and re-enable Google Play. These steps were able to eliminate xHelper from Amelia’s device. Let’s hope that this discovery brings the saga of xHelper to a conclusion.