Winnti Group Infected Hong Kong Universities With Malware
by Sergiu Gatlan
Computer systems at two Hong Kong universities were compromised in a Winnti Group campaign according to ESET researchers, during the Hong Kong protests that started in March 2019.
The attacks were discovered in November 2019 after the security firm's Augur machine-learning engine detected ShadowPad launcher malware samples on multiple devices at the two universities, following previous Winnti malware infections detected two weeks earlier, in October.
These attacks were highly targeted since the Winnti malware and the multimodular Shadowpad backdoor both featured command and control URLs and campaign identifiers related to the names of the impacted universities.
"The campaign identifiers found in the samples we’ve analyzed match the subdomain part of the C&C server, showing that these samples were really targeted against these universities," ESET said.
Three other universities also targeted
Based on the malware used in the attacks — the info stealing focused ShadowPad backdoor — the attackers' end goal was to collect and steal info from the compromised computers.
The ShadowPad variant discovered on the universities' infected devices features keylogging and screen-capture capabilities, provided to the malware by two of the 17 modules it comes with.
The use of a keylogger module enabled by default is a clear indication that the threat actors were interested in stealing info from their victims’ computers according to the researchers. "In contrast, the variants we described in our white paper didn’t even have that module embedded."
During this campaign, ShadowPad's launcher was replaced by the Winnti Group attackers with a simpler one that wasn't obfuscated with VMProtec and it used XOR-encryption rather than the typical RC5 key block encryption algorithm.
ESET thinks that three other Hong Kong universities were targeted in the same series of attacks by the Winnti Group threat actors.
"In addition to the two compromised universities, thanks to the C&C URL format used by the attackers we have reasons to think that at least three additional Hong Kong universities may have been compromised using these same ShadowPad and Winnti variants," ESET researcher Mathieu Tartare explained.
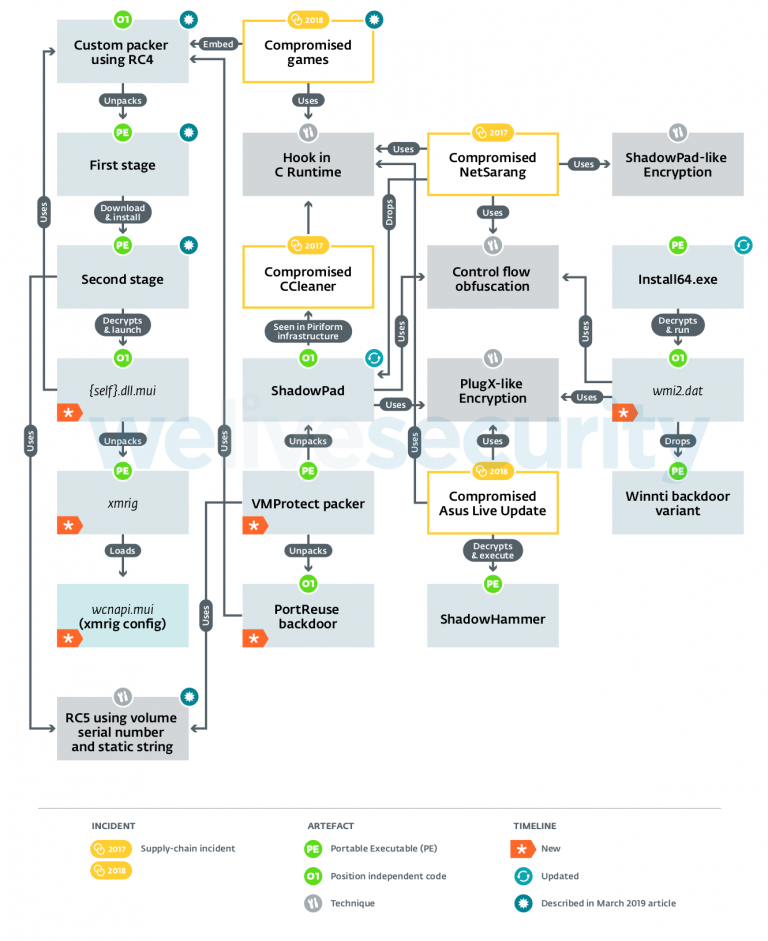
Winnti Group rundown
The Winnti Group is an umbrella term used as the name of a collective of Chinese state-backed hacking groups (tracked as Blackfly and Suckfly by Symantec, Wicked Panda by CrowdStrike, BARIUM by Microsoft, APT41 by FireEye) sharing the same malicious tools that have been in use since around 2011.
That is when Kaspersky researchers found the hackers' Winnti Trojan on a massive number of compromised gaming systems after being deployed via a game's official update server.
Kaspersky also uncovered evidence connecting the methods used by Winnti Group to compromise ASUS' LiveUpdate during Operation ShadowHammer with the ones utilized in other supply-chain attacks including NetSarang and CCleaner from 2017.
Winnti Group updated their arsenal with the new modular PortReuse Windows backdoor they later used to compromise the servers of a high-profile Asian mobile software and hardware manufacturer, as ESET found in 2019.