
Phishing scams leveled up, and we didn’t
Don’t be Jeff Bezos.
by Violet BlueMore than a bit of "I'm smarter than you" politics creates the divide between hacking headlines and what we actually need to worry about. On one side, researchers present findings at conferences hoping someone will raise the alarm and practical things will get done before things get worse. On the other, we have Jeff Bezos and his iPhone.
In case you missed it, on January 22nd The Guardian reported, "Amazon billionaire Jeff Bezos had his mobile phone 'hacked' in 2018 after receiving a WhatsApp message that had apparently been sent from the personal account of the crown prince of Saudi Arabia."
According to the now-contested report by FTI Consulting cited by The Guardian, that was in April. I was curious enough to notice that the "hey boi r u up" texts between Crown Prince Mohammed bin Salman and Jeff Bezos were exchanged before Jamal Khashoggi was murdered in October of that same year.
Questions, we have them. But Khashoggi's name is hard to find in the wider reporting about Bezos' iPhone -- which has been a mess from the start. Instead, a former Facebook security pundit and at least one actual researcher snatched the spotlight to say FTI's report was lacking in facts.

The self-appointed infosec "adults in the room" weren't wrong. But it was a pedantic and selfish distraction from anything that mattered about the whole affair.
Normal people read about the maybe hacking of Bezos' phone and shrugged. He can afford the best security on the planet. Saudi Arabia's Prince Claus von Bonesaw is a monster. Everyone's getting hacked, especially us peasants. These are all things we know.
What we also know is that the supposed phone hack came via an attachment. And if the hack happened, an attachment was clicked. It's the same way the City of Baltimore's computers and emergency systems at Hollywood Presbyterian Hospital were infected and locked with ransomware. And it's how consumers are losing identities and accounts from malware, learning how to send Bitcoin to grubby teenage boys in latitudes and longitudes unknown because of ransomware. Click a link. Look at an attachment. Download a file. That's it. An attacker went phishing, and now you're on the hook.
All that is from phishing, though what we hear about most are the breaches: attackers grabbing usernames and passwords from breach dumps, then using tools with cutesy names like SNIPR or STORM to automatically try it out on all of your accounts to see what works. Which they do, because Equifax used default passwords on sensitive information, Facebook was so busy lying to everyone it left the barn doors open and the City of New Orleans refused to believe cybersecurity is critical infrastructure.
So much for "the adults in the room."
I attended a recent hacking conference in San Francisco called Disclosure expecting a lot of the same fresh hells -- the "I'm smarter than you" guys competing for attention while alarmed researchers in the background are trying to tell us something's on fire.
I was not disappointed.
Apropos to what was happening (or not) to Jeff Bezos at that moment, I saw the talk "Initial Public Ownage: Trends in Phishing Techniques Across Sophisticated Threat Actors." Sounds boring, right? Nope.
According to jaw-dropping data presented by Proofpoint's Ryan Kalember, phishing is now the No. 1 attack of choice for cybercriminals. "Phishing is attractive for different reasons for the attackers that do have technical skills, because it scales really well," Kalember told Engadget via email. "The bigger groups, like the threat actor behind Emotet, have built the automation to do social engineering at the scale of millions of messages a day, and are very good are getting their relatively simple attacks (often documents with macros sent via already phished cloud email accounts) through security controls."
So what, you say? All the adults (who were in the room a minute ago) know not to click strange links to win a free iPad or log in at notgoogle.com or download the attachment from Lisa@FreePills. Who does that? Florida grandmas falling for Nigerian princes, surely.
This thinking is fine and good only under the conceit that getting pwned is for people who aren't as smart as you or that the cliques running security for your email clients have perfected their specious and occult magics of marking suspicious emails with big, fat, red DANGER warnings. The adults have it under control, you think. Gosh, there must be a lot of dumb people, you muse.
Turns out, you're pretty wrong on both counts.
If you got an email from a law firm saying "divorce papers" and it was a real law firm and the email contained a link to a document on that website, you'd probably have a very emotional reaction and click it. Kalember saw numerous examples and brought receipts.
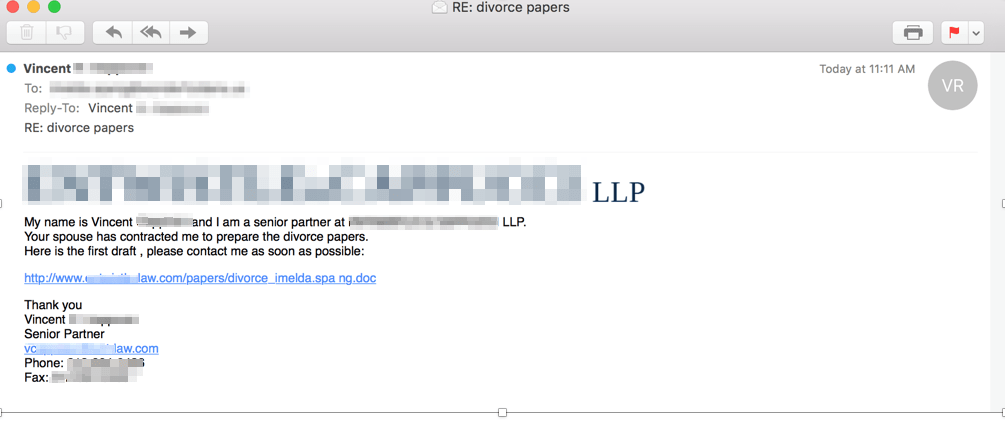
"In general," Kalember explained to Engadget, "the sneakiest phishes are highly socially engineered and customized for a specific intended recipient. The best example is a complaint about a specific person, sent to that person, which threatens to email (or even directly cc's) their manager. That said, we've seen threat actors use everything from fake food poisoning complaints, Greta Thunberg pledges, and Christmas party invites in just the last couple of months, so there's no shortage of innovation."
Right now around 1.3 million phishing operations reside illicitly on around 300,000 URLs. Ultimately it means many of us will be hacked/attacked because someone else's website security sucks.
So are all those WordPress hacks and vulns adding up or what? Kalember told us, "Compromising WordPress and other sites is unfortunately quite common, and it can be challenging for even the most experienced administrators to thoroughly clean as attackers often create layers of access." Explaining further, he added, "A tremendous amount of malicious content is also hosted on cloud file storage that most networks (and users) have to trust: SharePoint and OneDrive are the biggest offenders at the moment."
Every website that can be compromised -- hacked into -- is being used to send legitimate-looking phishing emails, using mail addresses from websites ranging from alpaca farms to law firms to universities.
Yes, actual alpaca farms. "While it's possible that the North Korean threat actor in question has a sense of humor," Kalember said, "it was a WordPress site that was vulnerable to an old exploit, so it was probably just opportunistic. From a network perspective, no one is likely to block their users going to alpaca farm websites, so it suits their purposes for command and control of their malware."
Criminal organizations are compromising legit sites and using those to send legit (and despicably personal) phishing attacks to install malware or ransomware. Often they want to compromise your employer or steal your accounts, because those are extremely valuable for doing more crimes. More to the point, thinking that you're not a target for any reason ("I'm not that interesting" or "I don't have followers/money" or "my job is boring") is going to make you the perfect target.
And looking at infosec trends (which tend toward sensationalism and know-it-alls), there's a serious lack of adults in the room to watch our backs. Kalember told Engadget, "Simply stated, attackers focus on people, and most defenders don't. Boosting awareness and email security controls are two practical ways to significantly reduce risk."
A wise and prophetic TV show called The X-Files once said, "Trust no one." This has never been truer than now. Rather than panic about every scary email or text message, treat all of your inboxes like your front door: If you're not expecting a delivery, don't open the door.
Images: AP Photo/Ted S. Warren (Jeff Bezos); Proofpoint (Malware email)