TrickBot Trojan Abuses Google Suite, Baits With Annual Bonuses
by Sergiu Gatlan
A recently active malicious campaign baited targets with phishing messages promising annual bonuses, abusing Google Suite cloud services to infect them with Trickbot banking Trojan payloads.
TrickBot (aka TrickLoader, Trickster, and TheTrick) is a modular information stealer regularly upgraded with new capabilities and modules since October 2016 when it was first spotted in the wild by Malwarebytes Labs' malware analyst Jérôme Segura.
This campaign's bait emails were sent using the legitimate SendGrid cloud-based email delivery platform in an attempt to conceal their malicious nature, as well as to obfuscate the links used throughout the infection chain as researchers at Palo Alto Networks' Unit 42 found.
The attackers employed embedded links to legitimate Google Docs documents that redirected the potential victims to a Google Drive download link. By clicking this link, the targets would be served with a downloader tool designed to drop the final Trickbot payload on the victims' computers.
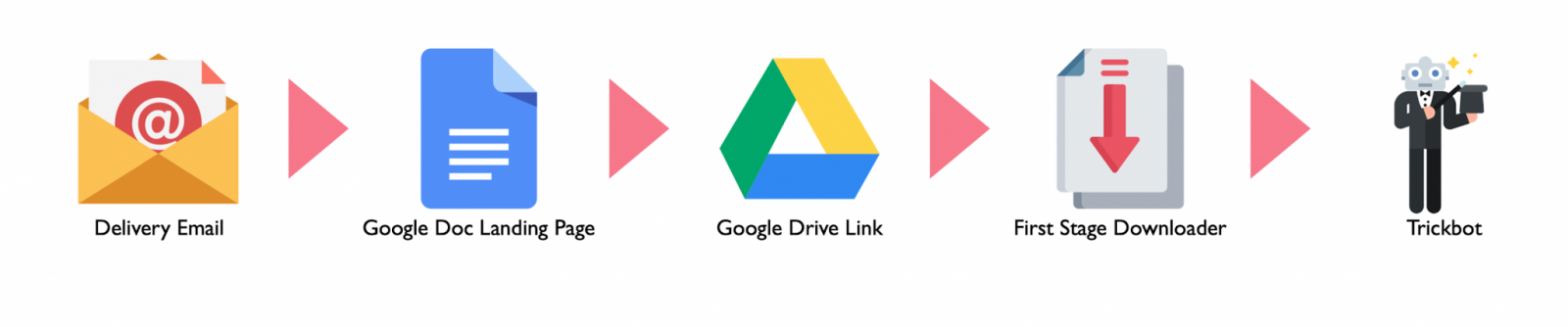
Delivering the Trickbot payload
The attackers used compromised .edu emails to send the phishing emails through SendGrid's Email Delivery Service (EDS) and bypass Secure Email Gateways (SEG) deployed on their targets' networks.
"The body of the emails contained lure text consistent with the subject lines and links that utilized a SendGrid function called Click Tracking which sends a notification back to the sender of the email for tracking purposes," the Unit 42 researchers discovered.
To deliver the Trickbot payloads, the campaign operators used two downloader variants, based on the phishing email's theme: StatementReport.exe in the case of annual bonus baits and Preview_Report.exe for payroll phishing messages.
"Due to default settings in most Windows deployments of not displaying file extensions, these files will not appear as obvious executables to a victim," the researchers add.
Once executed, the downloaders would display an "IMPORTANT" decoy pop-up asking the victims to update their Microsoft Word installation or to open the document on another computer.
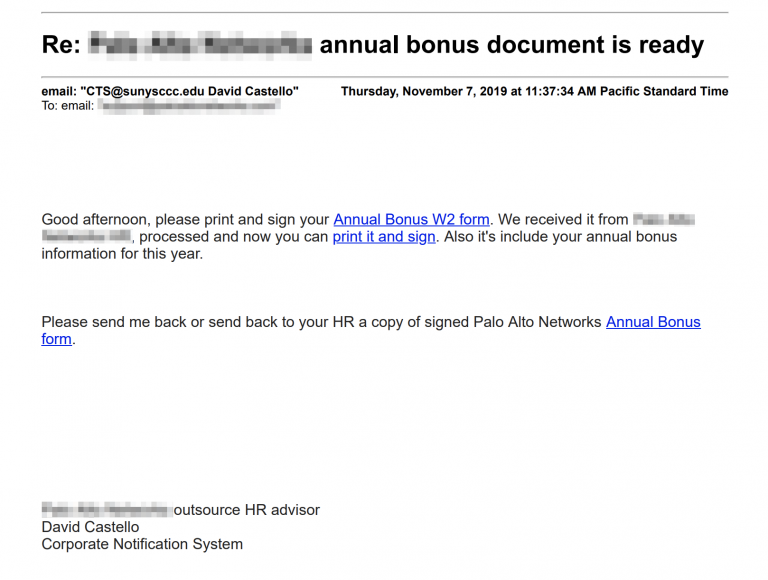
Trojan burrows deep into victims' computers
Regardless of what the victim does (dismisses the pop-up or not), the Trickbot payload gets dropped from first stage command and control (C2) servers owned by legitimate organizations — another attempt to avoid detection — to the Temp folder and gets executed.
Once launched, the Trickbot Trojan will load itself into memory using process hollowing after spawning a svchost.exe process to camouflage as a legitimate program and further attempt to evade detection.
Next, the malware starts collecting system information which it sends to its second stage C2 server and requests additional modules, while also gaining persistence by creating a "System cache service" scheduled task that auto-starts on logon and checks every 11 minutes if it's already running on a compromised system.
A full list of indicators of compromise (IOCs) related to this campaign and including downloader and payload samples, as well as Trickbot payload URLs are available at the end of Unit 42's report.
Continuously evolving banking Trojan
Last month, Unit 42's research team also spotted an updated Trickbot password grabber module that could be used to harvest OpenSSH private keys and OpenVPN passwords and configuration files.
The Google Docs online word processor was previously used in Trickbot campaigns as discovered by Cofense researchers in August when Trickbot payloads were delivered onto unsuspecting victims' devices via executables camouflaged as PDF documents with .pdf.exe extensions.
The phishing messages delivered via that malspam campaign used legitimate messages generated by sharing a Google Docs document with the targets, containing fake 404 error messages and links to the malicious payloads.
TrickBot is one of today's most aggressive malware after switching places with Emotet as the most distributed strain via malspam before the latter was revived during August [1, 2].