
Over 750,000 applications for US birth certificate copies exposed online
by Zack WhittakerAn online company that allows users to obtain a copy of their birth and death certificates from U.S. state governments has exposed a massive cache of applications — including their personal information.
More than 752,000 applications for copies of birth certificates were found on an Amazon Web Services (AWS) storage bucket. (The bucket also had 90,400 death certificate applications, but these could not be accessed or downloaded.)
The bucket wasn’t protected with a password, allowing anyone who knew the easy-to-guess web address access to the data.
Each application process differed by state, but performed the same task: allowing customers to apply to their state’s record-keeping authority — usually a state’s department of health — to obtain a copy of their historical records. The applications we reviewed contained the applicant’s name, date-of-birth, current home address, email address, phone number and historical personal information, including past addresses, names of family members and the reason for the application — such as applying for a passport or researching family history.
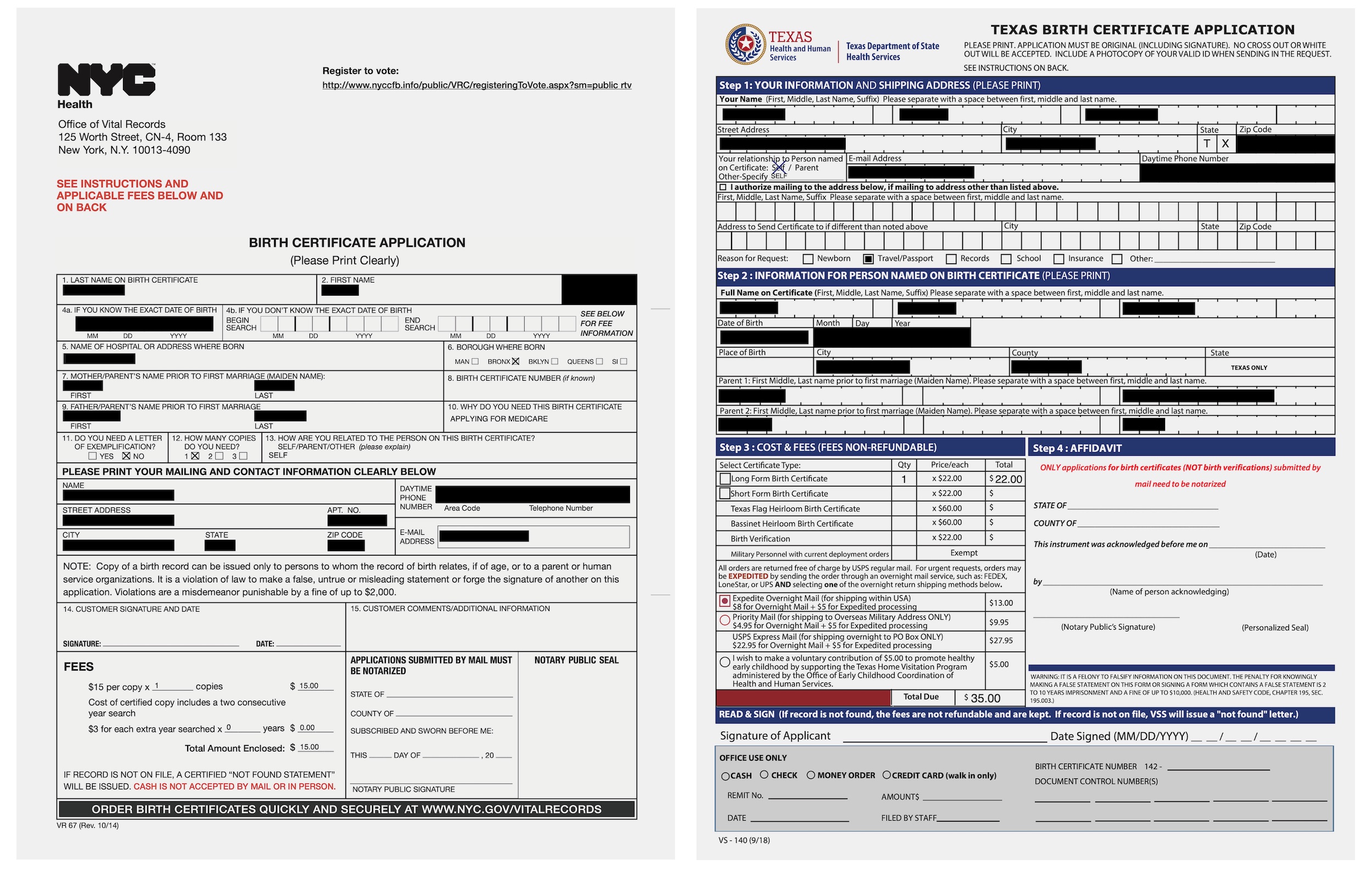
The applications dated back to late-2017 and the bucket was updating daily. In one week, the company added about 9,000 applications to the bucket.
U.K.-based penetration testing company Fidus Information Security found the exposed data. TechCrunch verified the data by matching names and addresses against public records.
Fidus and TechCrunch sent several emails prior to publication to warn of the exposed data, but we received only automated emails and no action was taken. We are not naming the company. When reached, Amazon would not intervene but said it would inform the customer.
We also reached out to the local data protection authority to warn of the security lapse, but it did not immediately comment.
Read more:
- Sprint contractor left thousands of US cell phone bills exposed
- Tuft & Needle exposed thousands of customer shipping labels
- StockX was hacked, exposing millions of customers’ data
- Stop saying, ‘We take your privacy and security seriously’
- Capital One breach also hit other major companies, say researchers
- Macy’s said hackers stole customer credit cards — again